The Concept of Least Rights
Microsoft recently noted that 77% of all vulnerabilities would be mitigated if the user did not have administrative rights. By removing the rights of users to ignore warnings and alerts, we ensure that the inbuilt safety mechanisms within Windows cannot be bypassed. This is critical as even legitimate software can ask for rights and accesses that it should not.
Unauthorised Software
Our experience has shown that once it is known that the IT Department is no longer required to install software, then software that’s outside of the normal approved software list is installed. Whilst the list of staff with access rights to install may be small initially, this list can grow and become unmanageable.
Malware Masquerading as Software
Some websites act as download hubs or links for software that can be obtained directly from the vendor. Whilst Google has got better in recent years, it’s still possible to buy advertising links that place your software above the legitimate vendor. The website either collects information from the download or worse, alters the download to contain malware.
From the list below, it’s not immediately clear what the correct download link is (2 searches for iTunes and Adobe Reader):
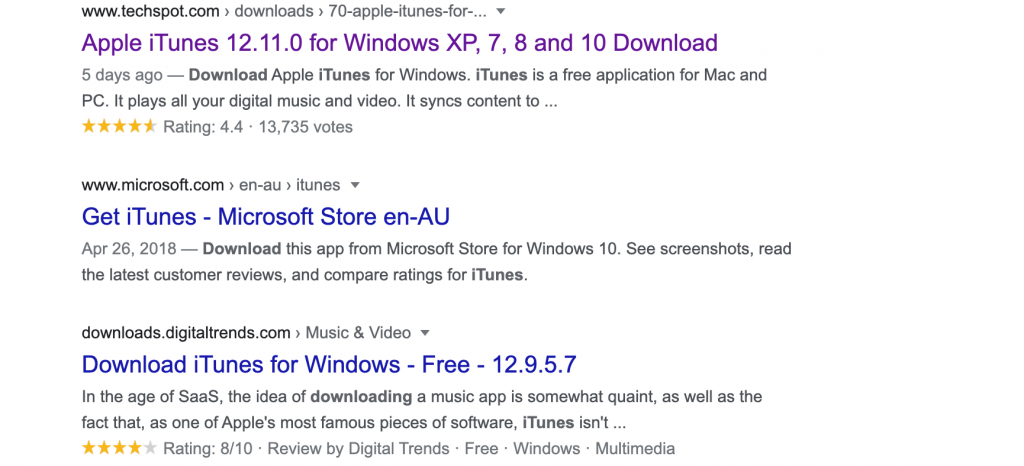
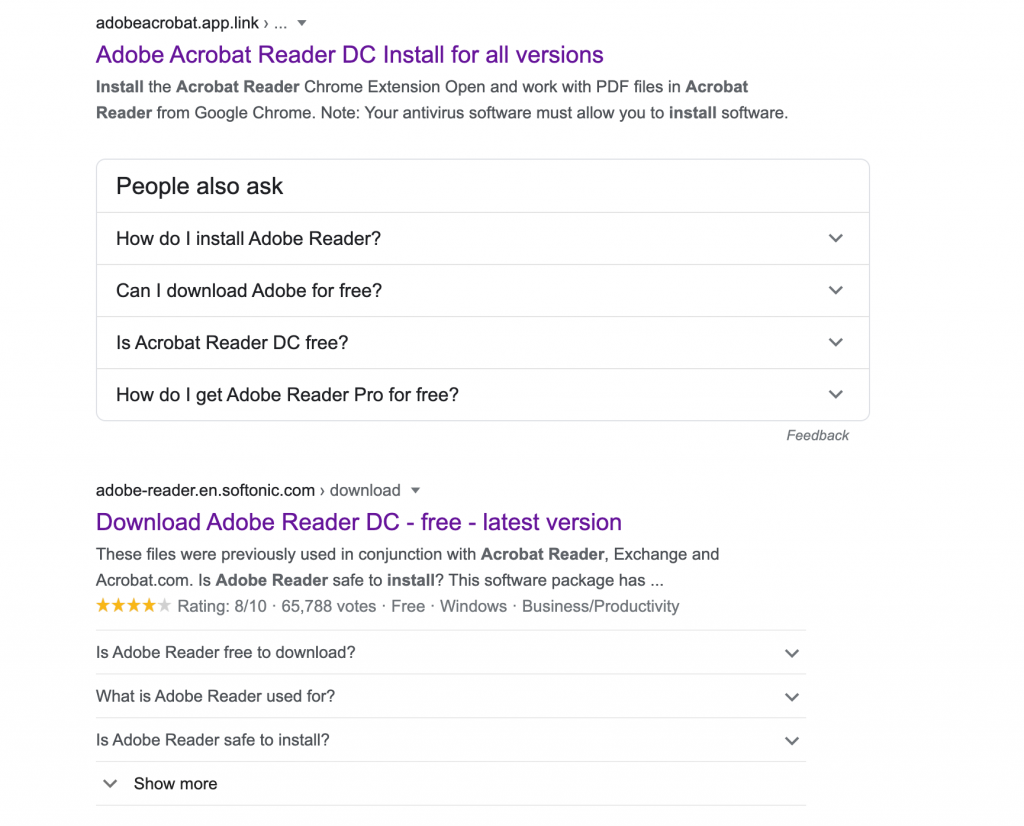
Even when the source is known and is legitimate, Adobe and others are renowned for packaging additional products with their software. It is not uncommon to see MacAfee ‘Free antivirus’ or Chrome add-ins that replace other key functions. The installers are sneaky and our technicians are trained in what to install or have access to enterprise installer versions that run far better than the normal desktop user install.
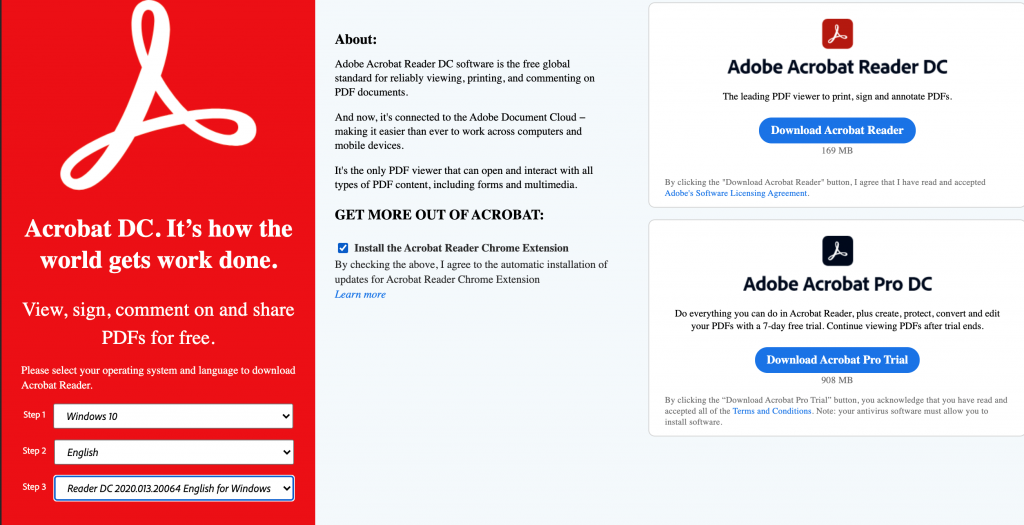
You can see from the attached that they pre-check the installer for the Google Chrome add-in and would prefer you download the 900MB Adobe Pro installer (which is hard to cleanly remove). This page is also hosted from their UK site, even if you go to it via the Australian site (and the download installer section is not listed at all, you need to know it’s at the very bottom of the page).
Persistent Presence
Should malware get installed on a device with admin rights, it will use those same rights to remove evidence of their presence. Assumptions can be made around other users and devices and lateral movement to other devices will take place, inbuilt protections disabled or reconfigured and other software installed. Most breach reports I have read all have as their starting point a single user who installed software and access to at least one other device inside the network.
Summary
My strong recommendation is that staff (even limited known users) are not provided with an Admin account as your network would be exposed to unacceptable risk from malware intentionally installed by staff who are trying to perform their normal operational duties (in other words, accidental, but intentional).
For help securing your business systems or to discuss this article in more detail, contact us today.
