
Excellence in Financial Services
Value Plus is a financial services company with a big mission: to provide individuals and businesses in Cairns with financial advice and financial management.
They have been successfully fulfilling that mission for many years via personal risk protection, wealth protection, investment planning, retirement advice, superannuation, self-managed super fund (SMSF), debt management, aged care, and estate planning.
Identifying Cybersecurity Vulnerabilities
Upon receiving a notification from a regulatory body outlining the risks associated with unmanaged devices, Value Plus began a comprehensive review of their existing cybersecurity protocols. They discovered potential legal liabilities under the Australian Privacy Principles (APPs) in the Privacy Act 1988 and identified the reputational risk and financial penalties that even minor security breaches could cause.
In an era where businesses are increasingly reliant on digital infrastructure and the risks of cyber breaches continue to grow, Value Plus knew it was time to bolster their cyber security defences.
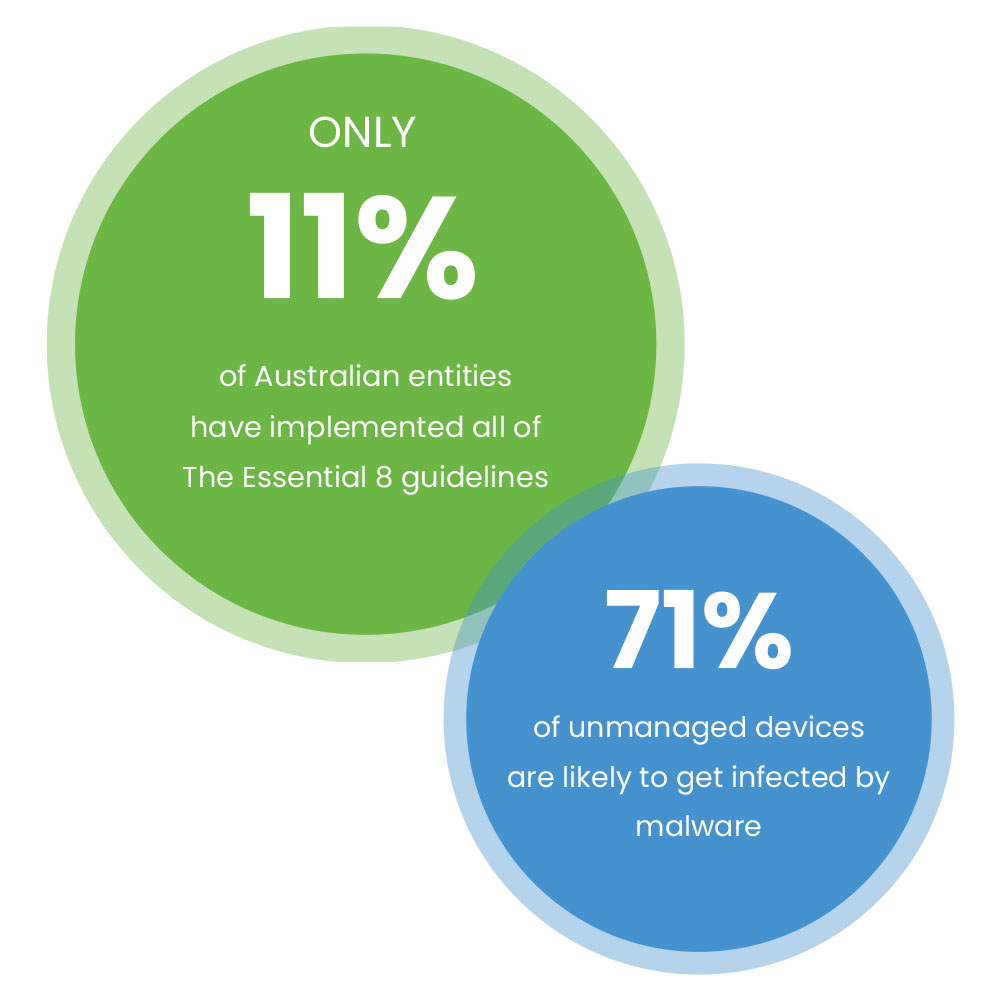
Alarmingly, Australian entities implementing all The Essential 8 guidelines at a managed level only make up 11%, indicating the widespread risk across the sector. And unmanaged devices are 71% more likely to get infected with malware. They can be easily breached “because they are invisible to security teams,” according to Moti Gindi, Corporate Vice President of Microsoft 365 Security.
The Journey to a Robust Security Solution
After an in-depth analysis of their situation, Value Plus engaged with Future IT Services, an IT and cybersecurity services company specialising in small business cybersecurity solutions.
Diagnosing the Current Cybersecurity Posture
Future IT Services initiated a thorough review of Value Plus’ cybersecurity posture, involving a review of logs, system requirements, staff interviews, and scrutinising regulatory documents. A week-long exhaustive investigation culminated in a detailed report, highlighting that Value Plus was partially compliant with the Essential 8 – baseline security strategies recommended by the Australian Cyber Security Centre (ACSC).
From Partial Alignment to Maturity Level 2
In response to the findings, Future IT Services devised a strategic plan for Value Plus to reach Maturity Level 2 compliance. The process involved gradual implementation – patching software, enforcing access controls, enabling multi-factor authentication, and developing an incident response plan. Additionally, they conducted a comprehensive training program for Value Plus’s staff covering strong password implementation and identifying potential cybersecurity threats.
Securing Data: Backup and Regular Review
Future IT Services also performed an initial data backup and scheduled subsequent regular backups. They ensured the consistent review and update of controls to safeguard Value Plus against evolving threats.
Successful Implementation and Enhanced Cyber Security
The implementation of the Essential 8 strategies offered a significant boost to Value Plus’ cyber security posture. Achieving Maturity Level 2 offered the team greater assurance in their ability to secure sensitive information and uphold the trust of their clientele. The investment in enhancing cybersecurity maturity effectively placed Value Plus in a stronger position to mitigate future risks.
Optimised Processes and Minimised Risks
Future IT Services not only helped mitigate the cybersecurity risks posed by unmanaged devices, but they also helped Value Plus become compliant with industry standards and reduce overall cyber risks. This initiative optimised client processes and call flows, allowing Value Plus to focus on their core business operations, securely.
We Help Businesses Like Yours
Download Our Brochure To See How
